Tenable Review: Is It Ultimate Cybersecurity Platform?

Worried about cyber threats lurking unnoticed? 😊
Tenable helps businesses find, fix, and reduce vulnerabilities before attackers can strike. 😍
Trusted by companies of all sizes, it gives you full visibility into your network cloud, on-prem, containers, and more.
With clear risk scores and insights, Tenable simplifies security, so you can stop guessing and start securing.
🎉 Tenable Deal – Get 20% OFF on Nessus Expert Today!
Save 20% instantly and secure your infrastructure with advanced attack-path analysis, cloud-config scanning, and expert-level threat detection. Limited-time offer!
🛡️ Can one platform really help you identify, prioritize, and eliminate risks before attackers even spot them?
In this Tenable Review, we break down its features, real-world performance, pricing, and whether it’s the right security solution for your organization.
Let’s dive in and see if it’s the right fit for you.
🔥 Limited-Time Offer – 20% OFF on Nessus Professional!
Grab 20% OFF on Nessus Professional and get enterprise-grade scanning, detailed reporting, and rapid detection for thousands of CVEs.
My Personal Tenable Experience 🤝
A few months ago, I helped a client in the tech industry struggling with network security.
They had tried several tools, but none provided the full visibility.
Setting it up was surprisingly easy, and within minutes, we had clear insights into their entire network cloud, on-prem, and containers.
In just a few weeks, their security was stronger, and they had real peace of mind knowing they were proactively protected.
Tenable made a complicated task feel simple, and I’m so glad I found it!
Why is Tenable Ruling The Market? 🤔
Tenable offers a comprehensive cybersecurity solution with several key features that make it stand out in the market.
Here’s a breakdown of the main features and additional ones to provide a deeper understanding:
1. Customer-first Culture
Tenable places a strong emphasis on understanding the unique needs of its customers, adapting to their evolving security requirements.
This customer-first approach ensures that the company continually improves its services based on real-world feedback, empowering users to better protect their systems without feeling overwhelmed by complex configurations or features.
2. Clear Business Alignment
Tenable ensures that its cybersecurity strategies align with your business goals.
It doesn’t just focus on technical aspects but also takes into account the business impact of each security decision, allowing companies to prioritize efforts that align with their broader organizational objectives.
This ensures security efforts are both efficient and effective, without wasting resources on low-impact vulnerabilities.
3. Rich Exposure Insight
With Tenable, you get a deep understanding of your network’s exposure to vulnerabilities. It provides real-time visibility across all assets, whether on-premises, in the cloud, or across hybrid environments.

This rich exposure insight helps identify weak spots, uncover hidden vulnerabilities, and track threats proactively, giving businesses the knowledge they need to take action.
4. AI-powered Excellence
Tenable leverages AI to enhance its vulnerability management capabilities.
Using advanced algorithms, it continuously analyzes data to predict and identify vulnerabilities and threats, even before they are exploited.
This AI-driven approach improves the accuracy and speed of threat detection and response, helping organizations stay ahead of emerging threats.
5. Broad Risk Vigilance
Tenable offers broad risk vigilance by continuously monitoring your entire environment, including networks, systems, cloud environments, and applications.

It doesn’t just look at vulnerabilities—it considers threats across the entire attack surface, making it easier to stay vigilant and prepared for any potential breach.
6. Comprehensive Asset Discovery
Tenable automatically detects and inventories all assets across your environment, whether they are in the cloud, on-premises, or mobile.

This ensures that no device or endpoint goes unnoticed, allowing organizations to have full visibility into their security posture and track all critical assets in real-time.
7. Vulnerability Scanning
With robust vulnerability scanning capabilities, Tenable identifies and evaluates vulnerabilities in your network before attackers can exploit them.

The tool scans in-depth across various operating systems, applications, and network devices to uncover weaknesses that need to be patched or mitigated, ensuring the system remains secure.
8. Continuous Monitoring
Tenable offers continuous monitoring of your environment, allowing for real-time detection of security incidents. With automatic alerts, you can respond quickly to potential threats as they arise.

This ensures that any new vulnerabilities or changes in the environment are immediately detected and addressed, minimizing risk exposure.
9. Compliance Management
Tenable supports compliance with industry regulations and standards, such as PCI-DSS, GDPR, HIPAA, and others.
It helps organizations stay on top of their compliance requirements by offering built-in templates and reporting tools.
This makes it easier for businesses to meet security and privacy standards without the added complexity.
10. Prioritization Based on Risk
Tenable’s vulnerability management system helps prioritize vulnerabilities based on risk levels, rather than just severity.
It considers factors like exploitability and the potential business impact of each vulnerability, allowing your security team to address the most critical issues first and minimize the risk to the organization.
11. Customizable Dashboards and Reports
Tenable offers customizable dashboards that let users view security data in ways that are most relevant to their needs. You can tailor reports to focus on specific vulnerabilities, assets, or threats, providing actionable insights in an easily understandable format for both technical and non-technical stakeholders.
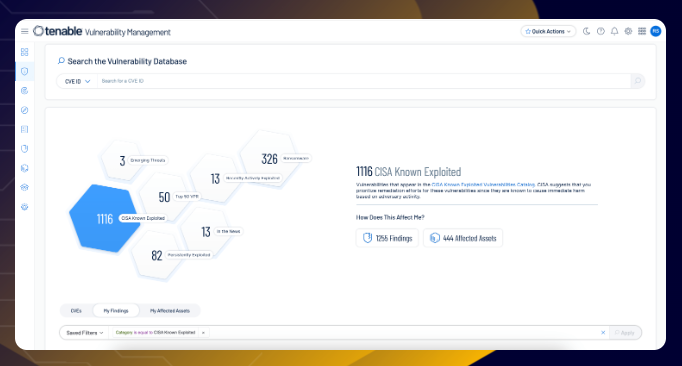
12. Automated Remediation
Tenable doesn’t just identify vulnerabilities—it helps automate remediation processes by integrating with other tools and platforms. This means that once vulnerabilities are detected, fixes can be applied automatically, saving time and reducing the chances of human error in the remediation process.

How to Access Tenable?: Step-by-Step📋
Step 1: Visit the Tenable Website – Go to Tenable’s official website to explore its product offerings and features.
Step 2: Click on “Buy” Option

Step 3: Choose the Plan – Select the exposure management product or solution that best fits your organization’s needs (e.g., Tenable One, Tenable Vulnerability Management, etc.).

Step 4: Enter your payment details, which may include: Credit/debit card information.
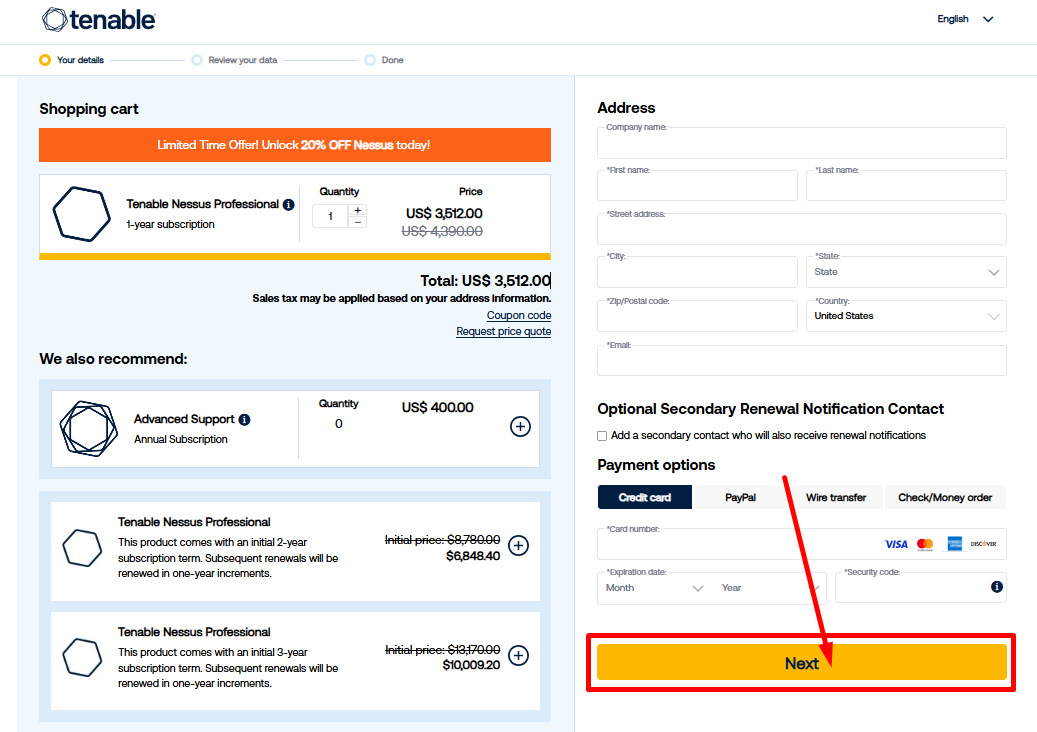
Step 4: Install the Platform – Once you’ve chosen your plan, Tenable provides detailed instructions on how to deploy its platform within your organization’s environment.
Step 5: Start Managing Exposures – Begin scanning your assets, analyzing vulnerabilities, and reducing risk with Tenable’s robust suite of tools.
Tenable Pricing Plans 💰
This is the advance pricing plan of Tenable according to which you can choose and can decide the pricing.
| Product | Subscription / License | Price (USD) |
|---|---|---|
| Tenable Nessus Professional | 1 Year License | $365.83 per month $4,390 total |
| Tenable Nessus Expert | 1 Year License | $532.50 per month $6,390 total |
| Tenable Vulnerability Management | 1 Year Subscription | $35 per asset $3,500 for 100 assets |
| Tenable Web App Scanning | 1 Year Subscription | $5,250 for 5 FQDNs |
Tenable VS CrowdStrike VS SentinelOne ⚔️
| Feature | Tenable | CrowdStrike | SentinelOne |
|---|---|---|---|
| Primary Focus | Vulnerability Management | Endpoint & Cloud Security | Autonomous Endpoint Protection |
| Threat Detection | Moderate, mainly exposure-based | Industry-leading real-time detection | AI-driven autonomous detection |
| Remediation Support | Prioritized vulnerability fixing | Guided response + managed services | Automatic threat mitigation |
| AI Capabilities | Exposure AI (risk-based insights) | Falcon AI + threat intelligence | Purple AI (autonomous SOC) |
| Ease of Use | Simple scanning & dashboards | Very intuitive, SOC-ready | Straightforward, automation-focused |
| Pricing | Starts at $3,500/year | Starts around $4–8 per endpoint/mo | Starts around $6–9 per endpoint/mo |
Tenable’s Vulnerability Management Capabilities
Tenable’s vulnerability management capabilities are a cornerstone of its platform. It enables organizations to identify, prioritize, and remediate vulnerabilities across a wide range of assets, including on-premise, cloud, and hybrid environments.
Here’s a detailed look at how Tenable’s vulnerability management works:
1. Vulnerability Scanning and Identification
Tenable performs deep, thorough scans across your entire infrastructure to identify security gaps and vulnerabilities. It uses a variety of scanning techniques to cover both common and advanced vulnerabilities:

- Credentialed vs. Non-credentialed Scanning:
- Credentialed scans allow Tenable to access systems with administrative credentials, providing a deeper, more accurate view of vulnerabilities within the system (e.g., OS-level vulnerabilities).
- Non-credentialed scans run with limited permissions and can identify vulnerabilities from an external perspective, such as open ports and unpatched software.
- Agent-based vs. Agentless Scanning:
- Agent-based scanning involves installing lightweight agents on endpoints, enabling continuous monitoring, even when devices are offline or behind firewalls.
- Agentless scanning uses network-based scans without the need for installing agents, suitable for remote assets or environments where agents are impractical.
2. Continuous Monitoring
Tenable continuously monitors your network for vulnerabilities in real-time. Unlike traditional vulnerability scanning, which is done periodically, Tenable’s continuous monitoring feature helps businesses detect and respond to new vulnerabilities as soon as they emerge, reducing the window of exposure. This includes monitoring for:
- New assets or changes in the network
- Newly discovered vulnerabilities
- Configurations or security posture changes

3. Risk Prioritization
Once vulnerabilities are identified, Tenable doesn’t just leave you with a long list of issues. Instead, it uses its powerful risk-based approach to prioritize vulnerabilities based on factors such as:
- Exploitability: How likely is it that a given vulnerability will be exploited? For instance, if an exploit is publicly known, it’s given a higher risk score.
- Impact on the business: Vulnerabilities affecting critical business systems or high-value assets are prioritized higher.
- Exposure level: Tenable looks at which vulnerabilities are most accessible from the outside or from less-secure parts of the network.
This prioritization helps security teams focus on the most pressing issues first and avoid wasting time on lower-risk vulnerabilities.
4. Contextual Remediation
Tenable provides actionable recommendations and steps for remediating vulnerabilities. These steps are contextual, meaning they are tailored to your environment and the specific asset or vulnerability in question.
- For example, Tenable will take into account which operating system is in use, which version of the software is running, and any known patches or fixes to suggest the most effective solution.
- Tenable integrates with popular IT Service Management (ITSM) tools like Jira, ServiceNow, and others to automate the workflow of remediation tasks, making the process faster and more efficient.

5. Automated Risk Assessment

Using machine learning and AI-powered algorithms, Tenable continuously assesses the risk associated with vulnerabilities, adjusting its risk scoring as new data becomes available. This allows organizations to have a more accurate, dynamic risk assessment model that adapts to the constantly changing landscape of cybersecurity threats.
Must Read: CrowdStrike Review: Is It Best Cybersecurity Platform?
Pros & Cons
| Pros ✅ | Cons ❌ |
|---|---|
| Comprehensive coverage across IT, OT, cloud, and AI. | Can be complex for beginners. |
| Advanced prioritization to focus on critical vulnerabilities. | Pricing may be high for smaller businesses. |
| AI-powered security with Tenable AI Exposure. | Learning curve for businesses new to exposure management. |
| Integrates with third-party security tools. | |
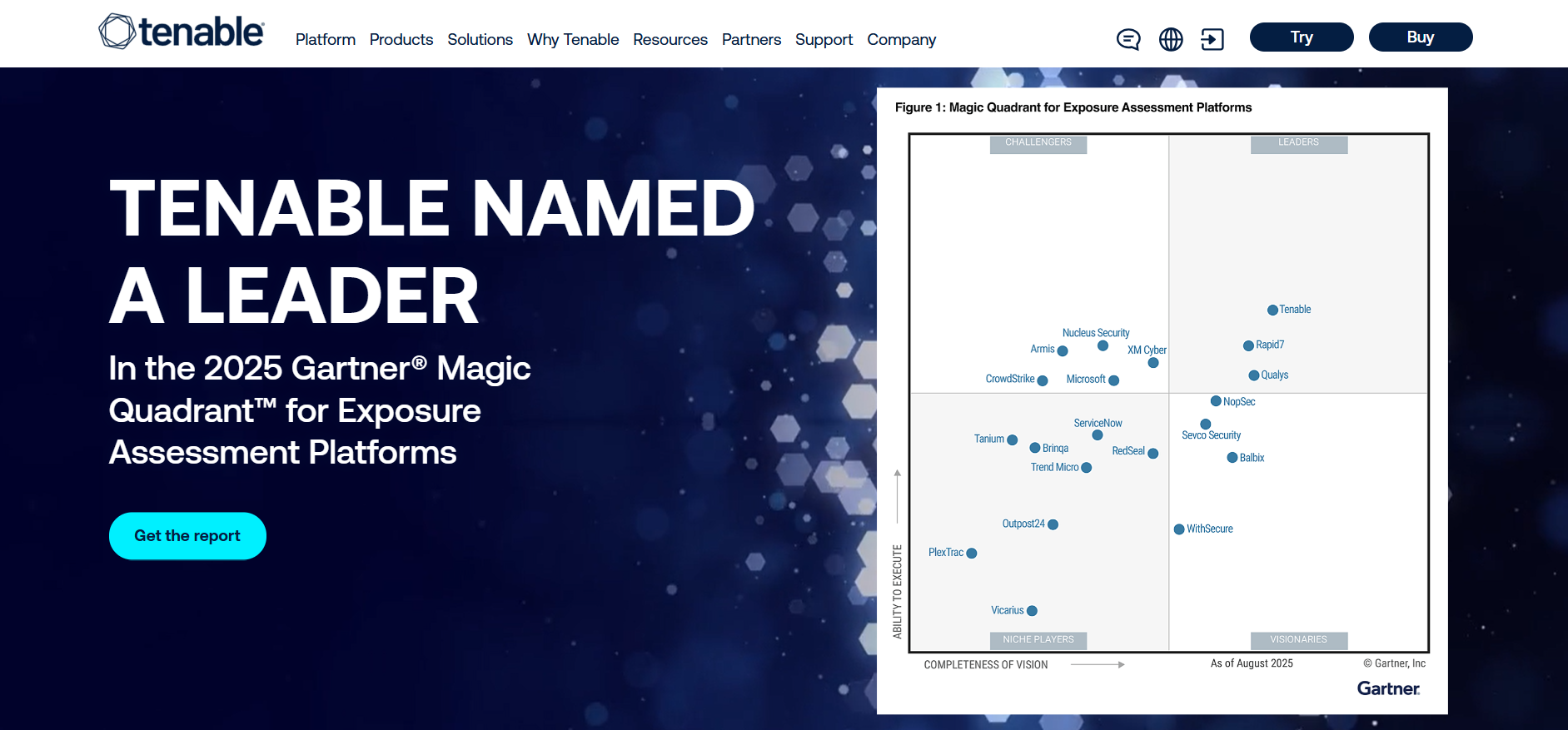
| Industry-recognized as a Customers’ Choice for Vulnerability Assessment (Gartner). |
Tenable Customer Reviews 🙋♀️


Final Thoughts: Is Tenable Worth It?📝
Yes! 100%, If you’re serious about taking control of your exposure management strategy.
Tenable is a powerful solution that can help you manage vulnerabilities, reduce attack surfaces, and protect critical assets across your entire environment.
Whether you’re a large enterprise or a growing business, Tenable offers the tools and insights needed to stay ahead of cyber threats.
Key Takeaways:
- Scalable solutions for businesses of all sizes.
- Comprehensive security across all domains: IT, OT, cloud, and AI.
- Proactive, AI-driven insights to help mitigate risk before it becomes a problem.
- Industry-leading recognition from analysts like Gartner and IDC.
FAQs 😊
Yes, Tenable offers robust vulnerability management for cloud platforms, including AWS, Azure, and Google Cloud, alongside on-prem and hybrid environments.
Tenable integrates with patch management tools to automate vulnerability remediation, saving time and reducing manual intervention.
Yes, Tenable offers continuous monitoring for real-time vulnerability detection, allowing quick responses to emerging threats.
Tenable is ideal for industries with complex security needs, including finance, healthcare, manufacturing, and government sectors.
Yes, Tenable offers customizable reports, which are easy to generate and share with different stakeholders.
